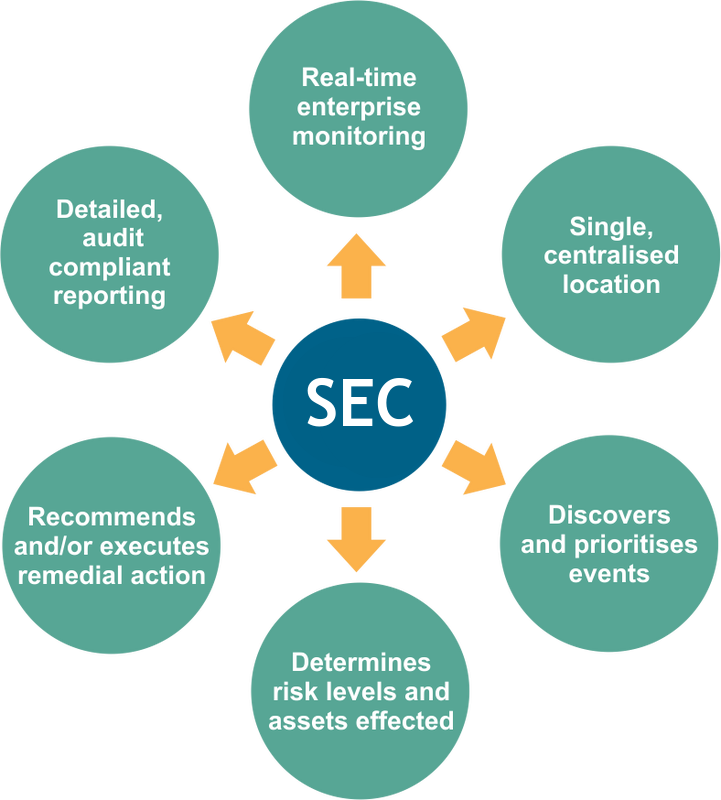
Security-as-a-Service | SECaas
✔ CASB - Cloud application security.
✔ SIEM - 24/7 visibility into your network environment.
✔ Testing - Assess vulnerabilities within your organization.
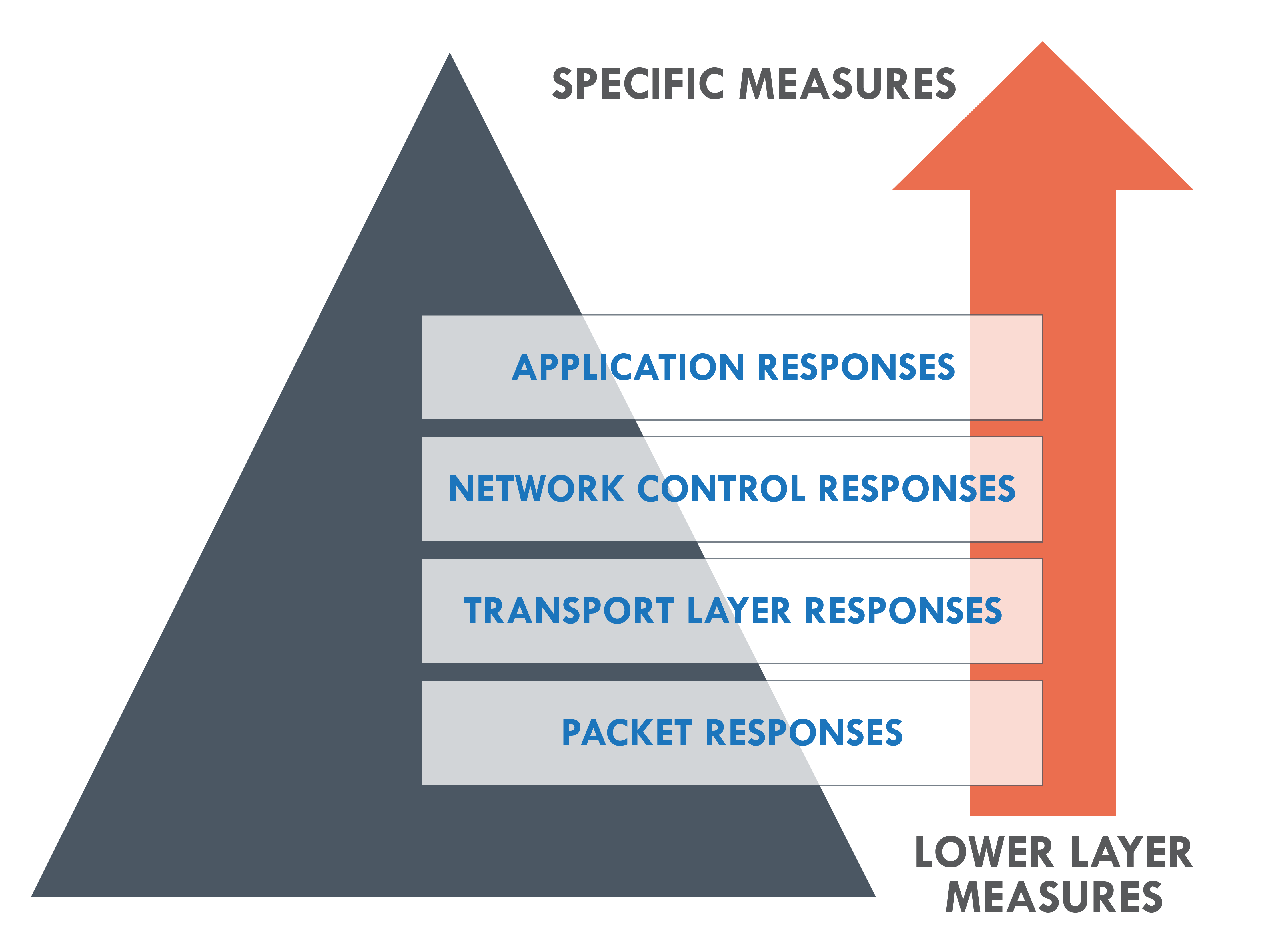
 INTRUSIONS
INTRUSIONS
Network anomalies, ransomware and targeted attacks.
 THREATS
THREATS
Rogue devices, authentication failures and cross-site scripting.
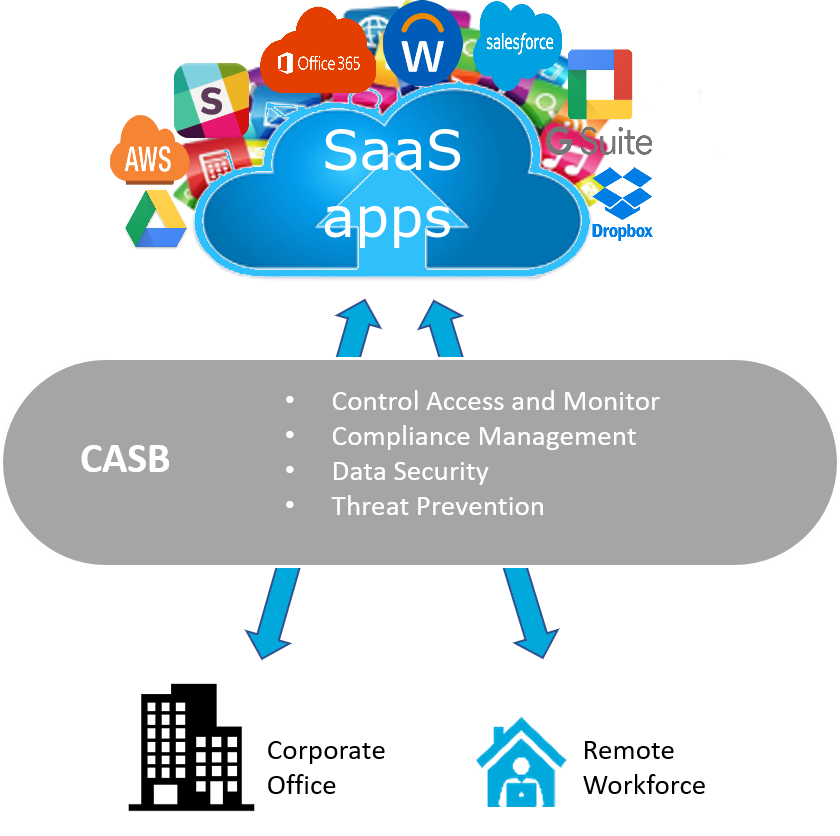
Shadow IT Protection
Cloud Application Security.
Comprehensive protection for SaaS based tools — trusted apps or unknown systems.
✔ Get granular visibility and control through integration.
✔ Block unsanctioned apps and services based on risk.
✔ Scan inbound, outbound and internal email in Office 365 and G-Suite.
✔ Prevent confidential file uploads and unauthorized sharing on OneDrive and Google Drive.
✔ Set consistent data security policies across applications.
✔ Monitor cloud usage with a single pane of glass dashboard view.
✔ Anti-phishing, attachment sandboxing and advanced URL protection.
✔ Protect SaaS environments against ransomware and zero-day malware.
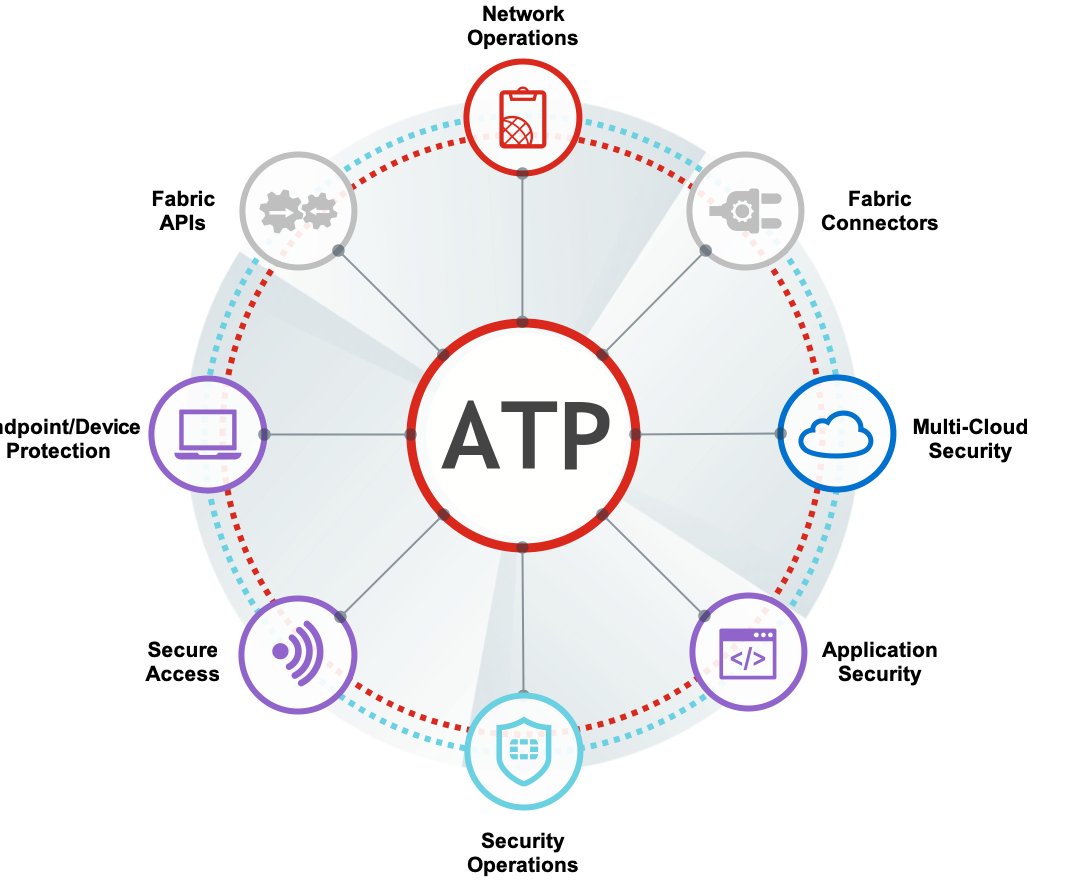
Advanced Threat Protection
ATP stops security threats at the edge.
A multi-layered approach to protect your network from all forms of attack.
✔ Extended firewall threat protection to detect and prevent zero-day attacks.
✔ Protection from email threats including ransomware, phishing and compromise.
✔ Safeguard your network from encrypted threats - inspection of TLS, SSL and SSH.
✔ Get detailed analysis of files being sent and received.
✔ Multiple operating system protection, including Windows and Android.
✔ Gain comprehensive visibility to malicious activity.
Assessment
Network Security Analysis.
Identify weaknesses and determine where additional resources need to be deployed to mitigate security risks.
✔ Vulnerability assessment, gap analysis and awareness.
✔ Website, application and penetration testing.
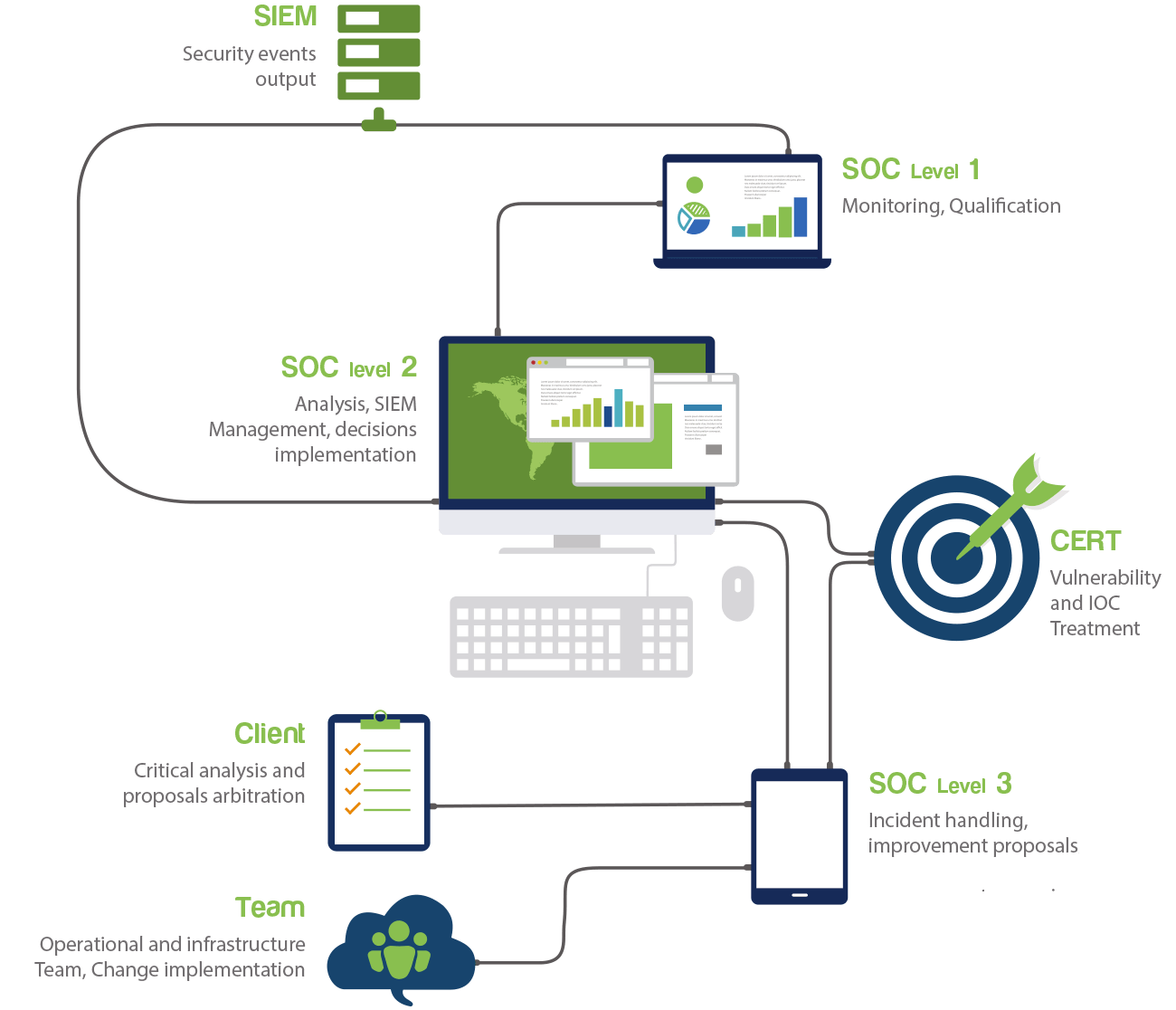
Incident Response
Investigation and root cause identification.
Our team helps you resolve your incident, returning your organization to normal network operations, and prevent recurring incidents, all while minimizing negative operational impacts and exposure.
✔ Management support and communication.
✔ Provides a comprehensive report of the incident.
✔ Show your staff how to manage these types of violations.
✔ Identify the cause and to create future prevention planning.
✔ Create an incident timeline of the matter.
✔ Deliver a full picture of cause, effect, and resolution during the event examination.
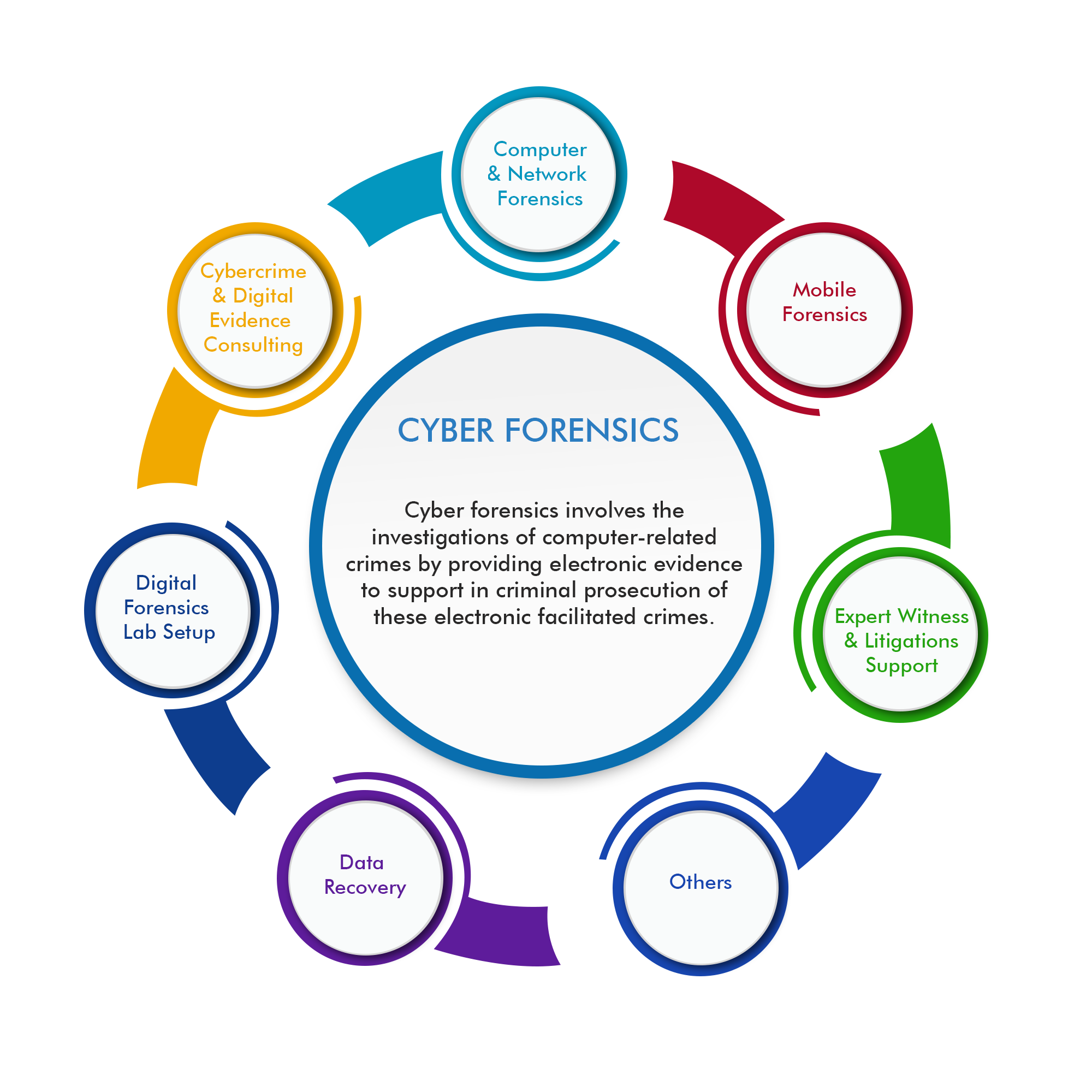
Digital Forensics
LANTECH offers our threat intelligence and log analysis to investigate the breach, determine the cause, provide reports and update progress to the appropriate parties, helping you contain and remove the threat from your environment as soon as possible.
✔ Analyze digital evidence for intellectual property theft.
✔ Provide expert testimony regarding forensic analysis finding for theft.
✔ Collection of electronically stored information (ESI) for litigation matters.
✔ Project management in the identification and preservation.
✔ Leveraged data loss prevention (DLP) logs to identify theft of clients’ proprietary information.