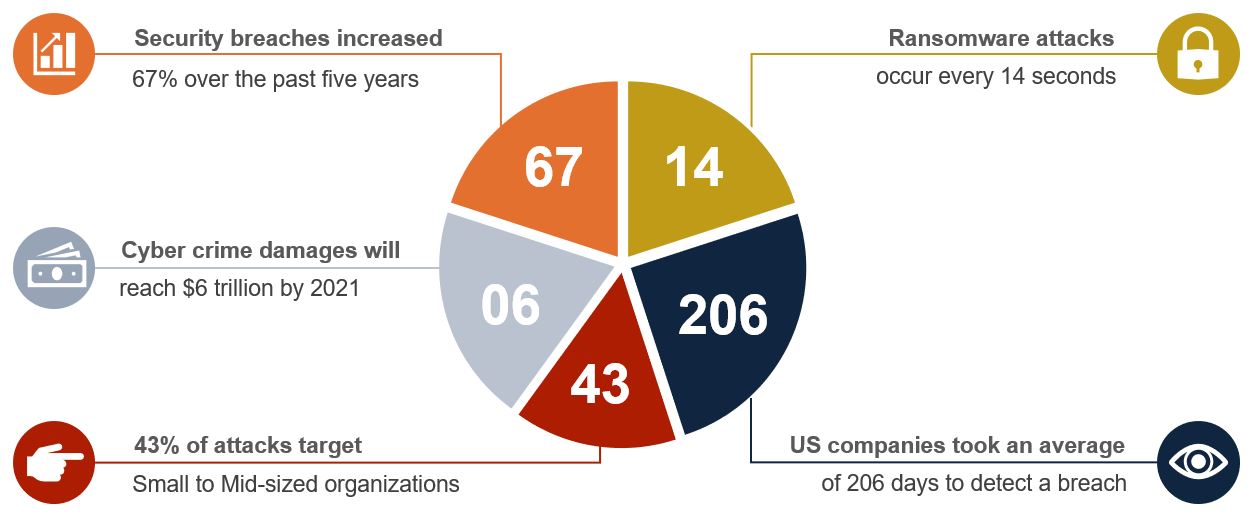
Security Assessments
SECaas identifies threats to your organization.
Leverage our security team, their experience and industry best practices to improve IT security and compliance requirements, while minimizing your staff and ultimately lowering your costs.
SEC-as-a-Service Benefits | SECaas
We understand securing your critical infrastructure.
 SECaas scales with your organization.
SECaas scales with your organization.
 Specialized security resources.
Specialized security resources.
 Enterprise threat intelligence.
Enterprise threat intelligence.
 Higher rate of detection.
Higher rate of detection.
 Saves time managing security.
Saves time managing security. Asset discovery and management.
Asset discovery and management.
 Compliance reporting.
Compliance reporting.
 Log analysis and retention.
Log analysis and retention.
 Improves security posture.
Improves security posture.
 Mitigate risks.
Mitigate risks.
Vulnerability Assessment
Vulnerability assessments should be a quarterly test as part of your security program. These types of assessments will identify where and how your environment is vulnerable to compromise. Running vulnerability scans on a quarterly basis will ensure you comply with most cyber security regulation standards and give you actionable recommendations on how you can lower your exposure. Our experience and approach will help you evaluate controls across your environment.

Risk Assessment
We recommend a risk assessment whenever there are significant changes to your information system or environment of operation or other conditions that may impact the organization. This could include upgrading applications, regime changes, upgrading infrastructure or moving to a cloud environment. Information risk assessments will identify security gaps and deliver actionable recommendations to improve network security, using the latest technology and industry best practices.
Website Security
Our website application penetration test is designed to help you follow best practices for web application security. Industry regulations such as PCI, HIPAA and Red Flag require website security. Protecting privacy and personal identifiable information (PII) has become top priority for most industries and countries. This type of an assessment evaluates the source code, the infrastructure, the operating systems, online payments processing integrations and software services, along with overall application functionality.

Application Security
Our approach provides a standard methodology for you to assess your applications and provide your developers an implementation guideline for securing application deployment. We provide technical recommendations with mitigating controls and policies and procedures to keep your applications secure over time.
Gap Analysis
Organizations are taking pro-active measures to protect themselves from constant attacks that are coming from all parts of the globe. Finding these issues (gaps) before the attackers will help you identify areas that need priority attention. We will review your existing framework against proven standards (PCI, NIST) to determine areas that need improvement.

Pen Testing
Penetration test is a growing component for cyber security regulation standards and to help identify security gaps in your environment. These are typically done on a yearly basis. We play the role of an attacker to exploit vulnerabilities, either in your employees or through the network or application to see how your existing security controls and policies stand up under “real world” conditions.
